Detecting CVE-2018-16983 (NoScript Bypass)
MORE INFO: https://nvd.nist.gov/vuln/detail/CVE-2018-16983
The following post is regarding information which is obviously quite old.
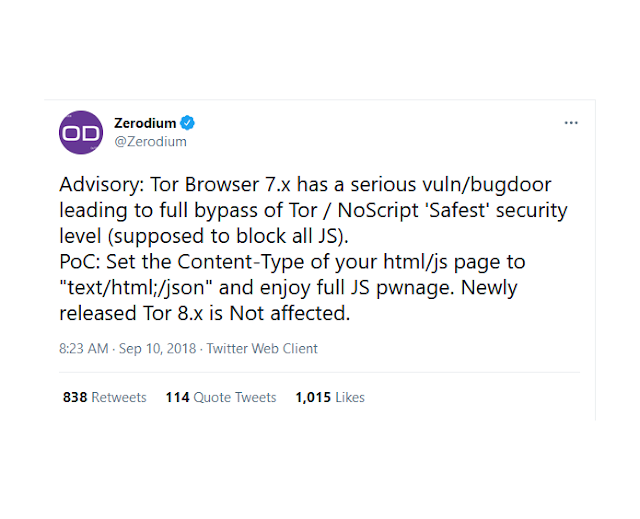
As a long time NoScript user, I was quite alarmed to see a tweet put out by Zerodium detailing an extremely simple exploit that tricks NoScript into allowing Javascript to be executed.
I consider NoScript necessary for a safe browsing experience. However, the real concern is for those whose physical safety relies on the security and privacy provided by the Tor Browser, which is by extension affected by this critical flaw.Unfortunately, I was unable to locate a version of NoScript (prior to version 5.1.8.7) that is vulnerable.
In any case, I am releasing the following Snort rule in hopes that someone may benefit from it.
alert tcp any any -> any any (msg:"EXTERNAL_NET CVE-2018-16938 NoScript Content-Type Bypass"; content:"text/html\;/json"; sid:1; rev:1;)
Fortunately, we may still the efficacy of this rule using netcat.
A stripped-down Snort configuration file was written for this exampe, as shown above.
Tcpdump is listening on the loopback interface, dumping traffic to a file named 'noscript.pcap'.
We created a simple text file as a proof of concept to demonstrate the exploit. The contents of the file are piped to a netcat listener on port 4444. Netcat is then reused to connect to port 4444, causing the exploit to be sent over the loopback interface.
Snort is then directed to log to the current directory, load the configuration file from the current directory, and read noscript.pcap from the current directory.
When the generated alert file is opened, we see that Snort was successfully able to detect the exploit.







Comments
Post a Comment