Blue Team Labs Online - Wargames
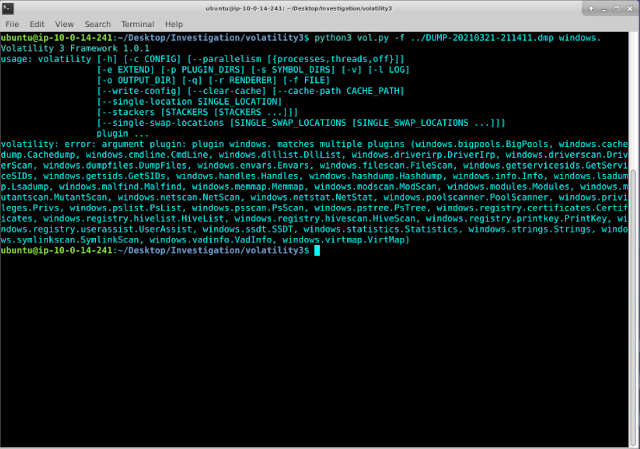
SCENARIO A privileged USER working as local admin on a "REALLY SECURE System" opened a HOWTO for the "TIC TAC TOE" Strategy Game. Unfortunately he downloaded the HOWTO from a repository controlled by an adversary named TRUDY. We suspect exploitation was performed on the system and that persistence has been achieved. After the user noticed his system was acting strange he disconnected it from the network and the local IR unit was able to acquire a memory dump using the “dumpit” tool. You have your disposal an updated version of the VOLATILITY 3 FRAMEWORK and linux cli to perform your analysis To view available windows plugins for volatility3 the following command may be used: python3 vol.py -f ../DUMP-20210321-211411.dmp windows. What was the System Time at time of Image Acquisition? (5 points) python3 vol.py -f ../DUMP-20210321-211411.dmp windows.info.Info The output shows the system time of image acquisition to be 2021-03-21 21:14:13 What's the Virtual Memory A...